Digital Fraud Schemes in Gaming: Tricks You Should Be Aware Of
Cybercriminals deliberately exploit platforms like Steam and Discord to trick unsuspecting users into revealing their login credentials. They frequently use modified and varied methods:
- Fake Playtest Invitations:
Users receive supposed invitations to game tests, such as for titles like "Mafia: The Old Country" or "Sand". These invitations lead to manipulated websites that prompt users to enter their Steam credentials, which are then intercepted. - CS:GO Gambling Sites:
Players are lured to unofficial gambling websites that promise attractive skins or winning opportunities. These sites often serve as traps where users can lose their valuable in-game items. - Discord Scams Involving Alleged Game Tests:
Messages from alleged developers circulate on Discord, asking users to test new games. However, the provided files contain malware designed to steal personal data and access credentials. - Fake Admin Warnings:
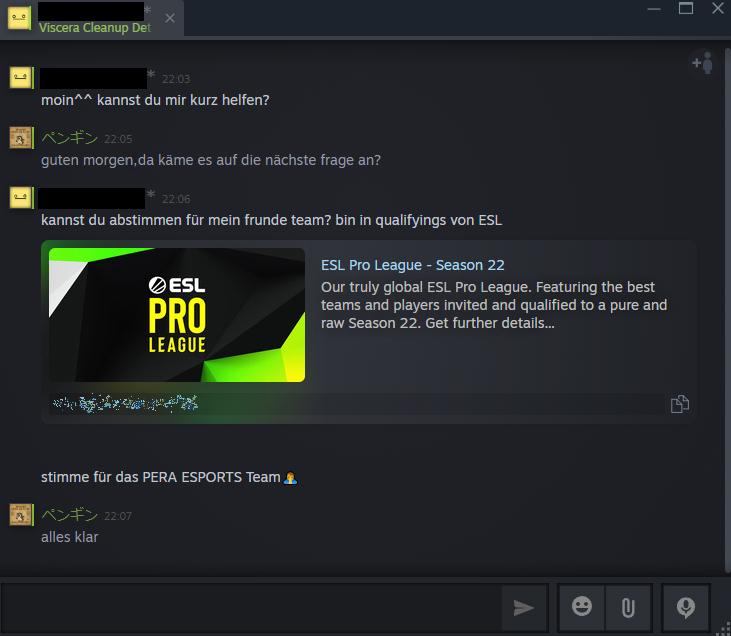
Fraudsters pose as Steam or Discord administrators, claiming that the user's account has been reported. They demand verification, attempting to obtain login credentials or money. - Vote for my team sites:
Users receive messages asking them to vote for a team in a tournament or competition. The included links lead to fake websites that mimic legitimate platforms like ESL, Steam or Discord. On these sites, users are prompted to enter their login credentials, which are then exploited by the attackers.
⚠️ From Click to Account Takeover: Risks from Fake Logins
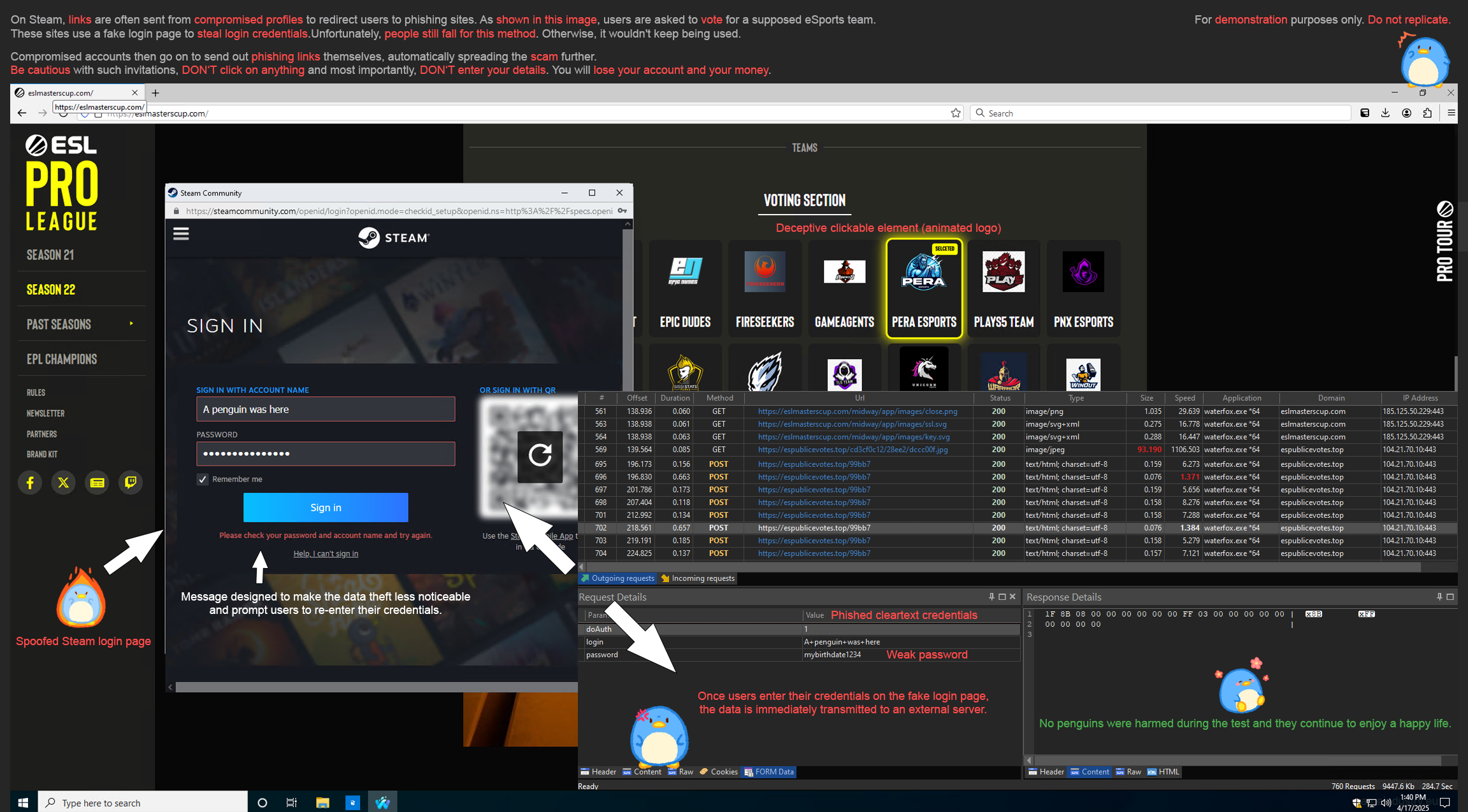
Credential Phishing via Fake Login Pages (Example: Steam Voting)
This social engineering method aims to deceive users into revealing their credentials through a deceptively genuine login page e.g. for Giveaways or Steam Votings. The pattern on these phishing sites is often the same and usually differs only in whether original (Steam)APIs and assets are accessed or not.
- Tempting Prompt:
Users receive a message or see a post containing an invitation with a link, e.g., "Vote for your team", "Win skins", "Join the playtest for XY". - Redirection to the Fake Login Page:
The link typically leads to a visually identical copy of a legitimate login page (e.g., Steam, Discord, Microsoft, etc.). - User Credential Entry:
Users enter their real credentials, believing they are logging into the original service. - Transmission of Credentials:
The entered data is transmitted in plain text to an external server controlled by the attacker. - Simulated Error Message:
After login, a message such as "An error has occurred. Please try again later." appears to mask the attack and avoid suspicion. In some cases, no effort is even made to translate the content into the target language. As a result, supposed error messages may appear in Russian or other languages.
- Access to accounts (e.g., Steam, Discord, email)
- Resale of stolen accounts
- Identity theft or use for further phishing attacks
- Spread of fraud methods
- Looting the account (money, items)
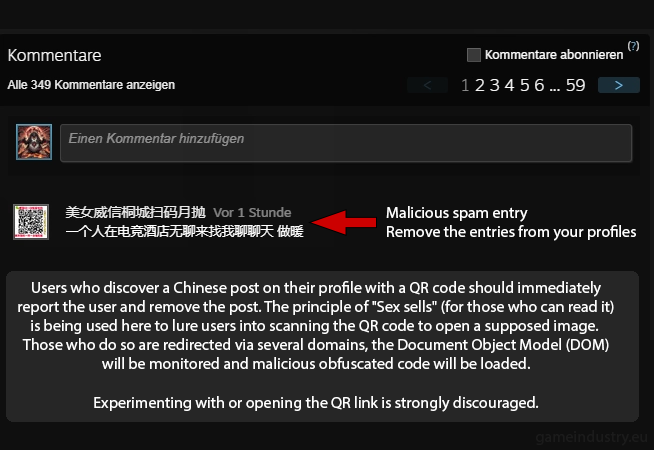
⚠️ QR Phishing with Drive-by Download via Redirect Chains
This attack method uses a seemingly harmless QR code to redirect users to a prepared website.
Tempting Text + QR Code:
A message (e.g., "Win now!", "Lonely/horny women are waiting for you", "Exclusive offer") is intended to encourage users to scan the QR code.
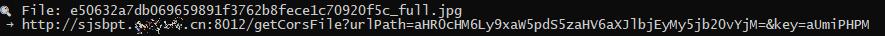
If you open the QR code, you will get a link like this one
ℹ️ A mix of Base64, ports and CORS requests. In addition, non-encrypted HTTP protocol
This allows others to eavesdrop on your traffic, as example in public networks
Do not open this or similar URLs in a browser or application.Redirection Through Multiple Websites and Malicious Code:
The profile's qr-code initially leads to an apparently harmless URL. This URL then automatically redirects the user through several steps, a so-called redirect chain. In the end, the user lands on a page that automatically loads or executes malicious code (drive-by download), such as malware or spyware.
The current malvertising campaign uses the obfuscation service JSJiami v7 to hide the code as well as the behavior from users.
One method used for this is reading and monitoring the Document Object Model (DOM) for purposes such as session hijacking, token theft, phishing, injecting fake login forms or extracting passwords.
Possible Attack Targets:
- Infection of the device with malware
- Theft of login credentials
- User surveillance
- Access to corporate systems
💡 General Safety Tips for Users
Act according to the "Zero Trust" principle: Never trust by default, always verify.
No device, person or file is considered trustworthy by default. Even if it appears to come from a legitimate source.
- Always check URLs carefully:
Fraudulent sites closely resemble legitimate ones but use altered domains (e.g., steamcomnunity.ru instead of steamcommunity.com). Always verify the spelling of URLs. When in doubt: do not click. - Never log in via external links:
Never enter login credentials after being redirected to a login page via Discord, email, chat messages, or QR codes.Steam, Discord, and similar providers will never ask users directly for their login credentials. Not in chats, and not via third-party websites. - Enable two-factor authentication:
- For Steam: Activate Steam Guard
- For Discord: 2FA using an authenticator app
- Be cautious with time pressure or threats:
Messages like "Your account will be suspended" or "You have been reported, click here to resolve" are classic pressure tactics. - Never trust files from unknown sources:
Even seemingly legitimate "playtests" or game demos can contain malware. Do not open .exe, .zip, or .scr files from Discord messages or forum posts. Playtest invitations and beta participations are not sent via chat. - Avoid permanent storage of login credentials:
Avoid storing login credentials permanently in your browser or on your devices, especially for sensitive accounts (e.g. Steam, Discord, banking). - QR codes are not inherently safe:
QR codes can contain disguised links. Only scan if the source is verifiable and trustworthy (e.g., official websites, product packaging). - Never accept screenshots as proof:
Fraudsters use fake screenshots ("You were reported...") to exert pressure. Platform operators never communicate via screenshots but through official messages in the account area. - Know official security warnings:
Discord, Steam, and others offer security pages explaining common fraud schemes. Discord, Steam, and others offer security pages explaining common fraud schemes. Check these sites regularly.
Official Sources
Steam Support: Recommended Trading Practices
Steam Support: Scam: I Have Been Reported and Will Be Banned
Steam Support: Account Security Recommendations
Steam Support: Scam FAQ (Confidence Scams and Trade Scams)
Discord Safety Center
Your opinion is important – please leave a comment!
2 Comments
lightwo
2025-04-19 18:29:29
I know these are all game-related scams, but something hilarious(ly concerning) I ran across posted around was a phishing technique that masquerades as a CAPTCHA, but prompts you to open the Run dialogue (Windows) and blindly paste a command into it.
I doubt that "CAPTCHA" ever goes past that state, but that's a hell of a way to get pwned for anyone who doesn't think a moment before doing. "Check yo' self before you wreck yo' self!"




















Pengin
2025-04-19 22:06:53
That’s certainly a really nasty method. I hadn’t come across it before either.
The target group probably also includes people who aren’t very tech-savvy, occasional users or online shoppers who don’t have the time, interest or energy to stay constantly informed. Or TeamViewer cases.
Especially now that tactics and methods are becoming ever more numerous and sophisticated in the "age of AI". And who gives much thought to a CAPTCHA/mechanic these days, especially since they have become commonplace.